You know how they say to save the best for last, well we have saved the worst for last…far worst. Up until a few weeks ago, Ransomware on the Mac didn’t really exist. It was like Bigfoot, you heard stories, but there was no hard evidence. There were rumors of some people in computer labs developing Mac Ransomware but it had never been spotted in the wild. Well, on March 4th 2016, that all changed when a compromised version of the BitTorrent client “Transmission” had a new nasty in there called KeRanger. All of a sudden, the Mac was now vulnerable to the worst kind of computer cancer out there, Ransomware.
Basically (and I’m oversimplifying) Ransomware encrypts files on your computer and it holds them hostage unless you pay the ransom. A dialog usually has a count-down clock and if you don’t pay by the time the clock runs out either your files are erased or the ransom will go up. Typically you have to make payment via bitcoin over the untraceable Tor network. If you don’t pay you will lose access to the encrypted files and no one can decrypt them without the key. If you do pay the ransom, you have to hope the horrible people will actually honor their part of the bargain and give you the decryption key but your chances are usually less than 50% that they will. Real Ransomware is super nasty and, as crazy as it sounds, there were reports that the actual FBI was advising that people just pay the ransom to get their files back. While some computer security professionals have said that paying the ransom was the least painful way to get your files back, the FBI’s actual advice is to visit the Department of Homeland Security’s U.S. Computer Emergency Readiness Team (CERT) CryptoLocker webpage for remediation information. I went there, sadly there isn’t too much there of help.
So what can you really do to protect your files? Well, the usual stuff comes to mind, just like with the other forms of Nastyware, be careful about what you do online and especially what you install. Don’t just blindly accept updates, make sure they are real and that you requested them. Don’t download any old software from just anywhere, know where your software is coming from and be sure it’s something you actually want. Be sure you stay current on your Mac Operating System, Apple has the latest and greatest protection built right into the OS. When KeRanger hit, Apple acted immediately and mostly-blocked it via Gatekeeper. Gatekeeper has been built into the Mac Operating System since Mac OS 10.7.5 Lion.
However my best advice is to keep a second Backup. That’s right, a second backup. Just one is not enough anymore (and if you don’t have a first backup you are really asking for trouble…) If Ransomware hits, it can encrypt data not just on your Mac’s primary drive but on any drive connected to your Mac. That means it could compromise your Time Machine backup drive just as easily as it did the primary drive. For the last few years, we have been urging customers to add an off-site backup like Backblaze to their mix. Backblaze has confirmed that their service would be a good form of protection in cases of Ransomware. Another alternative if you don’t want to use an off-site backup is to simply add a second Time Machine backup drive to your backup mix. Time Machine has had support for multiple drives since Mac OS 10.8 Mountain Lion. We would recommend buying a small, portable drive and hooking it up at some regular interval (every other week perhaps) and then keeping the drive disconnected from your Mac and in a safe location. This way, if your Mac ever were infected, your maximum loss is the time between the attack and the last not attached backup.
Thankfully, Ransomware on the Mac is incredibly rare so the likelihood of your Mac being infected is ultra-low. The flip side however is that it’s so horrible that protecting yourself is really important and smart. Having multiple copies of data and keeping that data off-site or in a safe place can help with other forms of damage too like catastrophic damage (fire, flood, theft, etc.) Lets all practice safe computing, surf smart, keep good backups and only get computer help from reputable sources.
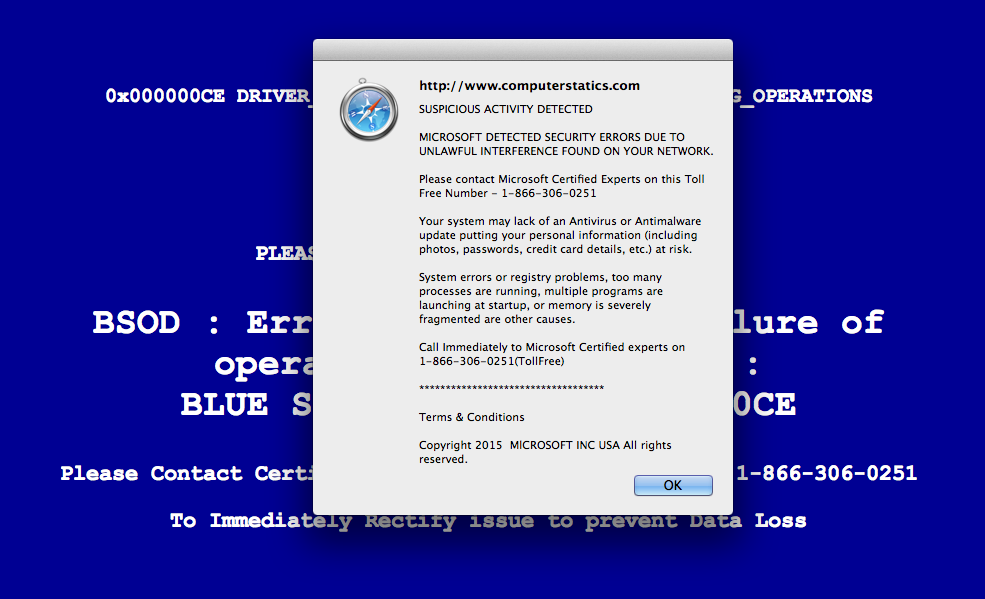
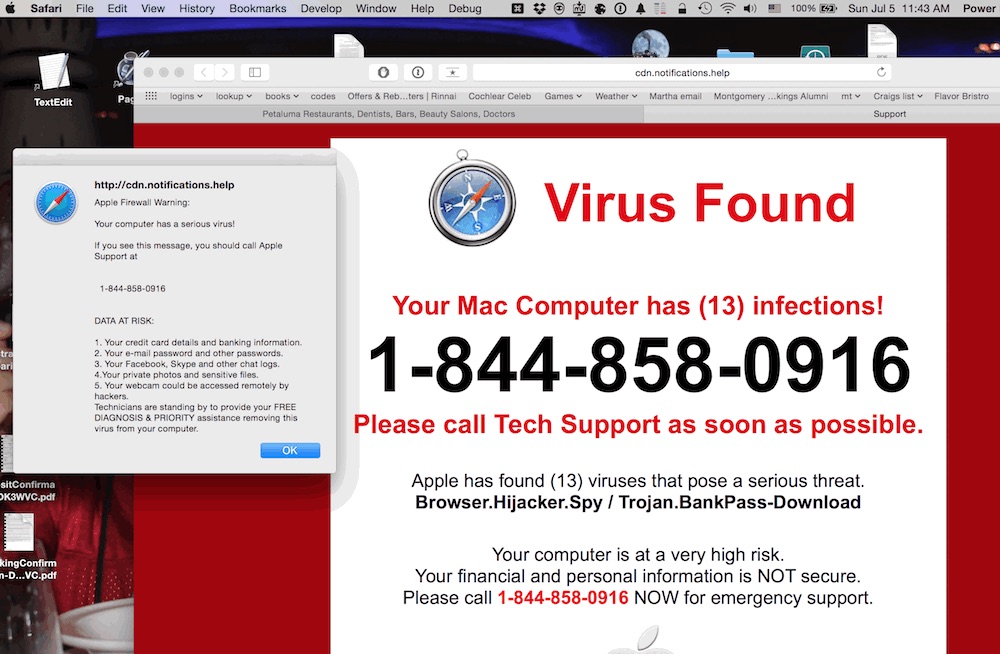
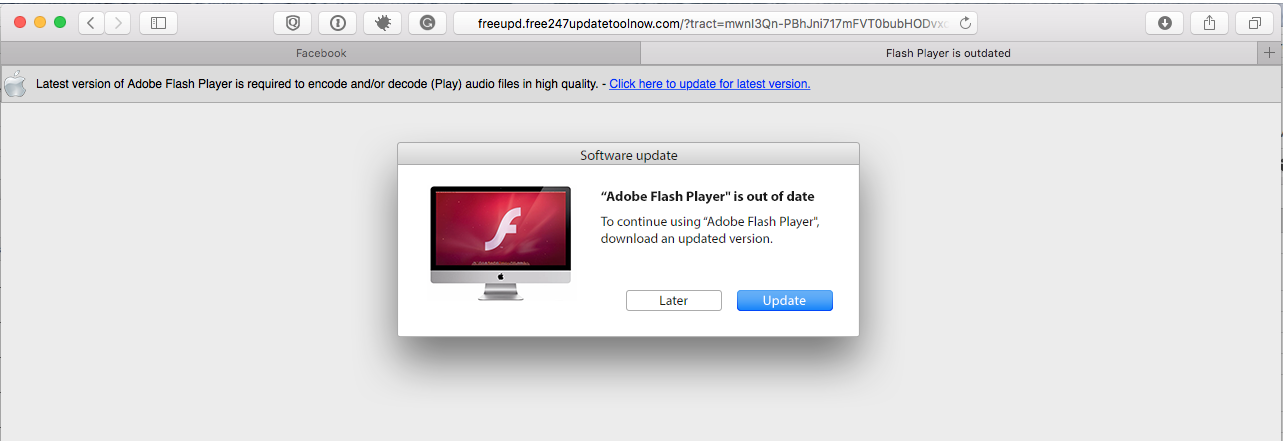
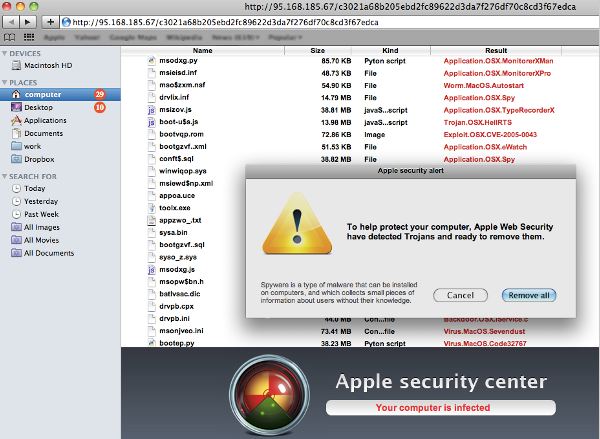
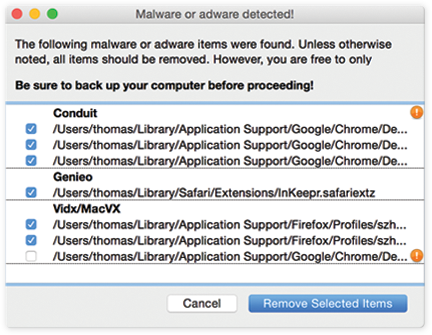
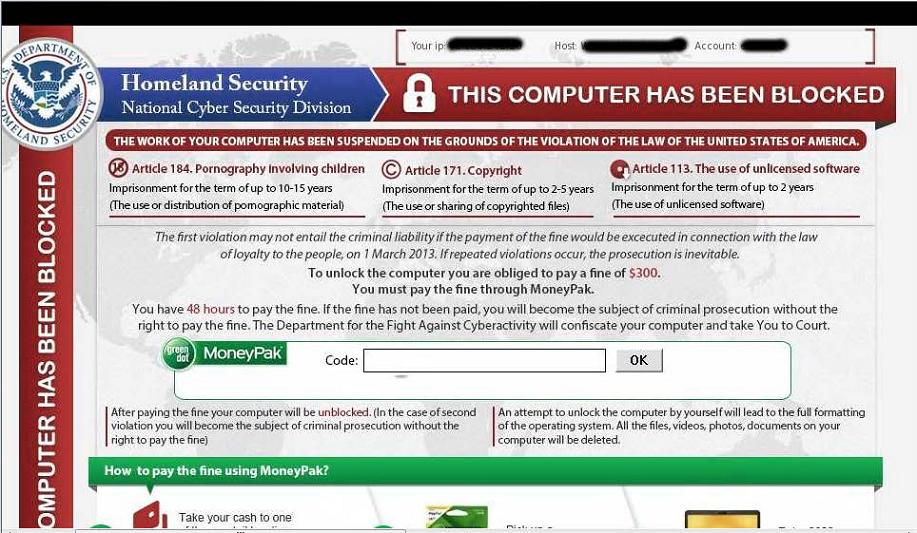
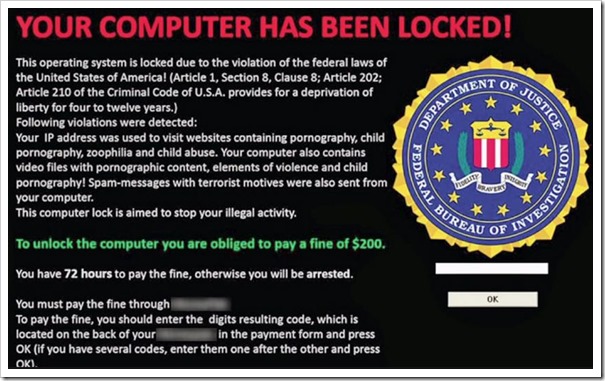
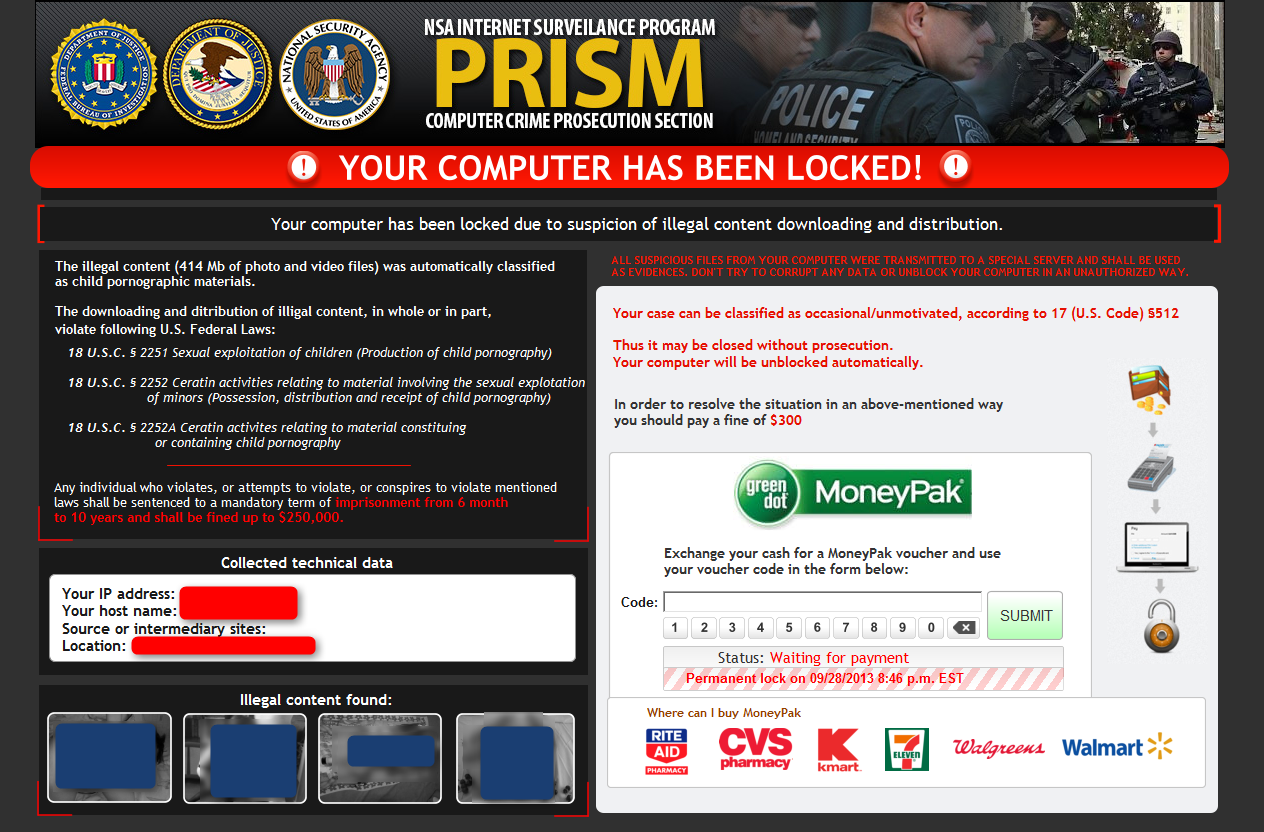
Here are some terrifying screen shots of Possible Ransomware, you do not want to ever see this on your computer: